Finally, a Truly Secure Approach to Threat Intelligence Exchange
jeffvaldes

My wife, who teaches first grade, would be the first to tell you of the many benefits of learning to share. One of the biggest? It helps build lasting trust among young children.
Building trust through sharing is equally beneficial for organizations — especially when it comes to cyber-related incident data.
In the world of cybersecurity, threat actors typically attack in parallel, targeting similar organizations simultaneously using nearly identical tactics, techniques, and procedures, or TTPs, in security parlance, to exploit the target environment. If organizations are willing to share near real-time details of an attack, in the form of actionable intelligence with other organizations which are further downstream, that gives those organizations a chance to prepare, reduce and possibly wholly negate the attack altogether.
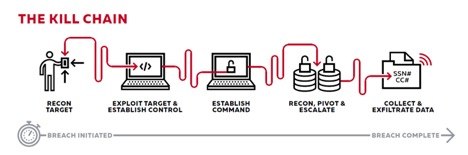
Consider the phases of a typical cyber-attack: threat actors initially spend time gathering intelligence and learning about their targets before making entry, like thief tracing your home a day or two before breaking in. The principal aim is to identify behavioral patterns, technical deficiencies and weakness that can later be exploited.
The good news is, threat actors often leave identifiable signatures. These signatures, if shared with downstream organizations, can be used as an early detection/warning system to prevent the threat from gaining a foothold within the environment before command, or exfiltration can take place.
Historical resistance, early attempts
With such a strong case for sharing, why would organizations be resistant? For a number of reasons, actually:
- Bad press/negative customer perception if made public
- Fear of industry or vertical competitors using the information to gain market share
- Perceived lack of defined governance structure
- Lack of mechanism to facilitate the secure exchange of incident related data
- Legal restrictions on third party sharing
Threat exchange was mandated by the federal government in 1998, resulting in the creation of Information Sharing and Analysis Centers, or ISACs, which were purpose-built to streamline the process of sharing event related data. Specifically, ISACs collect, analyze and disseminate actionable threat information to participating members. Today, more than 24 ISACs cover a broad swath of industry and government verticals.
In 2015, the Cybersecurity Information Sharing Act, went into effect, providing a legal process for federal agencies to share directly with commercial IT and manufacturing companies. Yet even with that mandate, and ISACs that provide a process to share information, many government agencies and private organization remain resistant.
Finally, however, a more secure approach to cyber intelligence sharing is being embraced by both public and private organizations, in large part because it offers what ISACs cannot: control.
Sharing without the risk
TruSTAR’s cyber intelligence platform allows users to share event data internally, across security, fraud and abuse teams, as well as externally, without the fear of exposing organizations to the perceived risks associated with incident sharing.
TruSTAR provides a secure and controlled environment so users can share meaningful cyber event data safely, easily and early in the response process. Because the system is secure, all types of data, such as open source, ISAC, and other commercial feeds can be corroborated in real time. This in turn exposes relevant insights that allow teams to investigate early and quickly. The cyber intel is correlated and enriched and it integrates well with key IT and security tools, including, security information and event management, case management and orchestration.
Before sharing an event, TruSTAR’s platform uses machine learning to extract, normalize and correlate data with intelligence reports supplied by other users across a vast collective of intel. If similarities are discovered, users are then alerted and provided with reports that contain additional attack indicators, observables, valuable context and even mitigation advice. Users might also decide to collaborate in other ways, such as joining in on response efforts.
“It’s time to take a page from attackers and share what we know,” said Paul Kurtz, co-founder and CEO of TruSTAR. “TruSTAR and partners like Rackspace are making sharing event data an integral part of their risk and mitigation process, rather than happening after the threat has been resolved. Event information can be shared quickly, and collaboration can begin early to stop threats have infiltrated others.”
Earlier this month, Kurtz was named CEO of the Year by Cyber Defense magazine, one of four Cyber Defense Global Awards TruSTAR earned, along with Next-Gen Threat Intelligence, Cybersecurity Blockchain, and InfoSec Startup of the Year.
What’s in it for me?
When it comes to sharing cyber incident data, organizations are not only suspicious of risk, they often don’t understand the potential value of sharing info. With TruSTAR’s platform, users are incentivized to upload reports in order to receive correlated reports, indicators of compromise and visual depictions of similar known threats reported by other users, and a global network of threat intelligence feeds, such as Crowdstrike, NIST, Splunk, Homeland Security, US-Cert, Facebook Threat Exchange and others.
Seeing the platform in action can really help organizations appreciate the results. In my previous role at Rackspace, I worked with the TruSTAR platform for two years, and am still amazed by the depth of the results we get.
The visual intelligence seen in TruSTAR’s Enclaves — flexible, secure, permission-controlled data repositories of security and threat intelligence information — ties all the correlated indicators, observables and other intel to provide the line of sight needed to draw the right conclusion.
The platform helped speed up our investigative process by allowing teams to dive into any surfaced path to eliminate less relevant possibilities. The normalization and correlation across the timeline is so powerful that users can go forwards and backwards and see how, when and where an exploit made its initial breach and how it worked through the kill chain.
Learn more about how Rackspace can help secure your infrastructure. And for more information about cyber exchange best practices, download the Cloud Security Alliance’s recent research paper, Best Practices for Cyber Incident Exchange.

Recent Posts
ViVE 2024 Attendees Explored the Leading-Edge of Healthcare Technology in Los Angeles
March 5th, 2024